Unknown Facts About Risk Management Enterprise
Wiki Article
The 6-Second Trick For Risk Management Enterprise
Table of ContentsRisk Management Enterprise - QuestionsRisk Management Enterprise - An OverviewThe Ultimate Guide To Risk Management EnterpriseEverything about Risk Management EnterpriseRisk Management Enterprise Can Be Fun For EveryoneThe Definitive Guide for Risk Management EnterpriseIndicators on Risk Management Enterprise You Should Know
Right here are several of its essential attributes that centers must understand. So, take a look. Real-Time Risk Evaluations and Mitigation in this software allow organizations to continually keep an eye on and review threats as they evolve. This feature leverages real-time data and automatic evaluation to determine possible threats promptly. Once risks are recognized, the software helps with instant mitigation activities.
They attend to the challenge of recurring threat administration by offering tools to keep track of threats constantly. KRIs boost safety risk oversight, ensuring that possible dangers are recognized and handled efficiently.
A Biased View of Risk Management Enterprise
IT take the chance of monitoring is a part of business threat administration (ERM), developed to bring IT risk in line with an organization's threat appetite. IT risk management (ITRM) includes the policies, procedures and modern technology needed to reduce risks and vulnerabilities, while maintaining conformity with appropriate governing needs. Additionally, ITRM looks for to limit the repercussions of devastating events, such as protection violations.While ITRM structures supply valuable support, it's very easy for IT teams to suffer from "framework overload." Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. Ltd., recommends using a combination of structures to attain the most effective outcomes. For instance, the ISACA Danger IT framework straightens well with the COBIT 2019 framework, Rose said.
Enterprise Risk Management Software Advancement: Conveniences & Qualities, Cost. With technological developments, dangers are continually increasing. That being claimed, organizations are more probable to encounter challenges that influence their financial resources, operations, and reputation. From quickly rising and fall markets to regulatory changes and cyber hazards, services browse with a continuously transforming sea of risks.
Our Risk Management Enterprise Ideas
In this blog site, we will dive into the world of ERM software application, discovering what it is, its advantages, functions, and so on to ensure that you can develop one for your organization. Venture Danger Monitoring (ERM) software program is the application program for preparation, directing, organizing, and managing business activities and streamlining threat monitoring procedures.With ERM, companies can make informative decisions to enhance the total durability of the business. Read: ERP Application Growth Devoted ERM systems are critical for businesses that frequently deal with vast amounts of delicate details and numerous stakeholders to approve critical decisions. Some industries where ERM has become a typical system are healthcare, finance, construction, insurance coverage, and information innovation (IT).
: It is stressful for any enterprise to go through a comprehensive audit. Nonetheless, it can be stayed clear of by utilizing the ERM software system. This system automates law conformity administration to keep the organization protected and certified. Various other than that, it also logs and classifies all the documents in the system making it less complicated for auditors to examine processes a lot quicker.
3 Easy Facts About Risk Management Enterprise Explained
You can also attach existing software program systems to the ERM using APIs or by adding data manually. Services can make use of ERM to review risks based upon their potential influence for much better risk management and mitigation.: Including this feature enables customers to get real-time notices on their gadgets about any type of risk that could take place and its effect.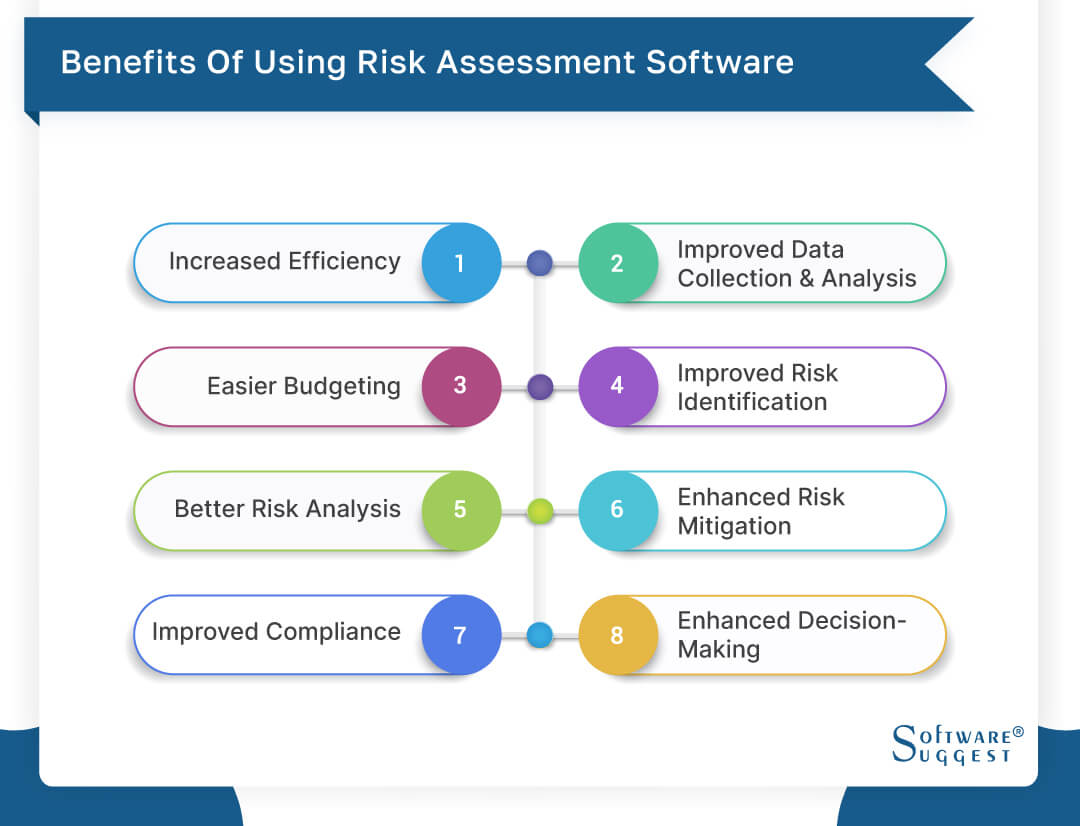
Instead, the software application enables them to establish limits for various processes and send push alerts in case of feasible threats.: By integrating information visualization and reporting in the personalized ERM software program, services can gain clear understandings about danger patterns and performance.: It is required for organizations to adhere to industry compliance and regulative requirements.

These systems make it possible for firms to apply best-practice risk monitoring procedures that straighten with market criteria, providing an effective, technology-driven approach to recognizing, evaluating, and mitigating threats. This blog explores the benefits of automatic risk management devices, the areas of threat administration they can automate, and the value they give an organization.
The Basic Principles Of Risk Management Enterprise
Teams can establish forms with the appropriate areas and conveniently produce different forms for different threat types. These danger assessment forms can be circulated for completion via automated workflows that send out alerts to the relevant team to finish the kinds online. If kinds are not completed by the target date, then chaser emails are instantly sent by the system.The control tracking and control screening procedure can likewise be automated. Firms can utilize computerized process to send regular control examination notices and staff can go into the results using on the internet kinds. Controls can also be kept track of by the software program by setting rules to send out signals based upon control information kept in other systems and spreadsheets that is drawn right into the platform using API integrations.
Danger administration automation software program can additionally support with danger coverage for all levels of the venture. Leaders can Risk Management Enterprise see reports on threat exposure and control efficiency with a range of reporting results consisting of static reports, Power BI interactive reports, bowtie analysis, and Monte Carlo simulations. The ability to pull live reports at the touch of a switch eliminates strenuous data control jobs leaving threat groups with even more time to assess the information and suggest business on the very best program of activity.
Organizations operating in affordable, fast-changing markets can not afford hold-ups or inefficiencies in addressing prospective dangers. Conventional threat administration making use of hands-on spreadsheet-based processes, while acquainted, commonly lead to fragmented data, taxing coverage, and an enhanced likelihood of human mistake.
Little Known Questions About Risk Management Enterprise.
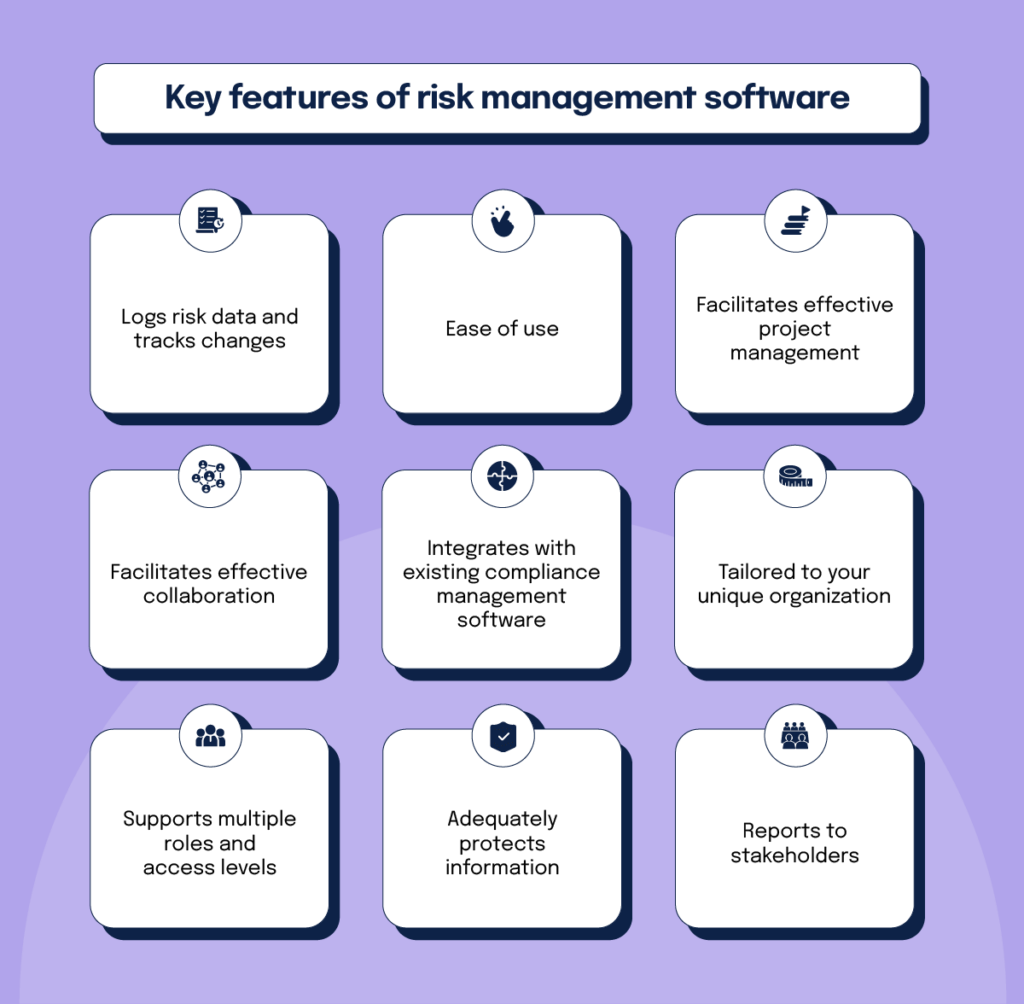
This makes certain threat registers are constantly present and lined up with business goals. Conformity is an additional critical driver for automating threat monitoring. Standards like ISO 31000, CPS 230 and COSO all supply assistance around threat administration ideal methods and control structures, and automated threat administration tools are structured to line up with these demands helping companies to meet most generally used danger monitoring criteria.Look for danger software systems with an authorizations power structure to conveniently establish up workflows for risk acceleration. This functionality allows you to customize the sight for each and every user, so they only see the information appropriate to them. See to it the ERM software program supplies individual tracking so you can see who entered what information and when.
Decide for a cloud-based platform to make sure the system obtains routine updates from the vendor adding brand-new functionality. Seek out tools that provide project threat monitoring abilities to manage your jobs and profiles and the connected dangers. The benefits of embracing risk administration automation software expand far past efficiency. Services that integrate these services into their ERM approach can expect a host of tangible and abstract.
The Single Strategy To Use For Risk Management Enterprise
While the instance for automation is compelling, carrying out a threat management platform is not without its challenges. For one, information high quality is crucial. Automated systems depend on exact, updated information to provide meaningful insights. To overcome the difficulties of threat administration automation, organizations must buy information cleaning and administration to guarantee a solid structure for carrying out an automated system.Automation in threat management equips businesses to transform their technique to risk and develop a more powerful structure for the future (Risk Management Enterprise). The inquiry is no much longer whether to automate risk management, it's how soon you can begin. To see the Riskonnect in action,
The answer often exists in how well dangers are expected and handled. Project management software offers as the navigator in the tumultuous waters of task implementation, offering tools that identify and examine dangers and devise approaches to minimize them effectively.
Report this wiki page